Keeping Your Campaign Secure with Hilary Stohs-Krause | Hello Merge Tag Ep 10
There’s an old joke: two campers are in the woods. One is hanging by the fire, the second comes running into the area, yelling about a bear while hurriedly putting on his shoes. The first camper says, “Do you really think you can outrun the bear?” The second camper says, “No, but I think I can outrun you.”
That joke came to mind while talking to Hilary Stohs-Krause, a senior software engineer at a cybersecurity startup who focuses on the intersection of tech, entrepreneurship and social good.
You don’t have to have perfect internet security to keep yourself and your campaign or organization safe. Your goal should be, in Hilary’s words, to “Make it hard enough [to hack you] that they’ll leave you alone.”
In her free time, Hilary’s a primary organizer for Madison Women in Tech and a board member for Madison Wisconsin’s Forward Festival.
I’ve known Hilary for years. We actually co-created a community called Madison Tech and Social Impact, that brought together folks in the tech space looking to volunteer their skills with those working in nonprofits or on causes-based issues looking for technical help.
Hilary knows a ton… about a ton!
But I invited her onto the pod to talk about digital security.
We covered a ton of ground, including:
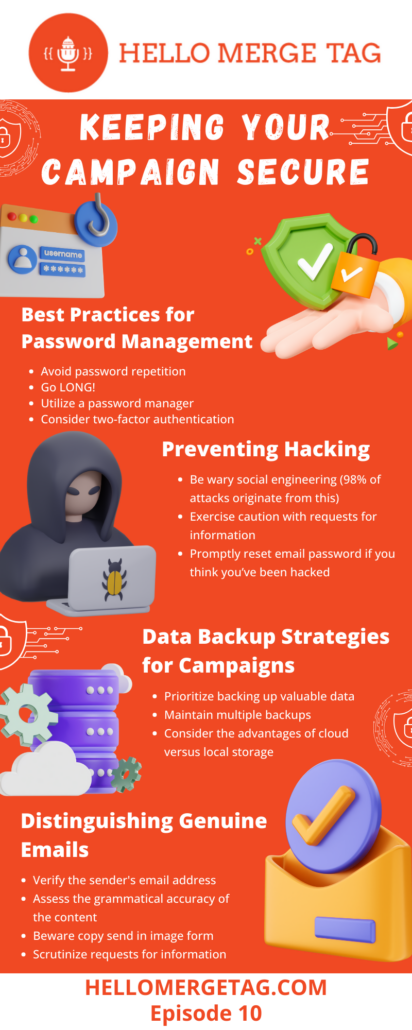
- The importance of unique passwords (as well as long passwords!)
- The power of a password manager
- The importance of two-factor authentication (2fa) and things to consider when setting yours up
- The danger of social engineering and how to watch out for it
- The benefits of paranoia when it comes to sharing personal data
- How and when to back up your data
- When to update your devices immediately, and when to wait and let the kinks get worked out
And a whole lot more!
You can connect with Hilary on her LinkedIn page.
Listen right here or wherever you stream podcasts:
Find all episodes at HelloMergeTag.com or wherever you stream podcasts.
Campaign Security Tips – An Infographic
- Keep your passwords long, never repeat them, use a password manager and use two-factor authentication for anything it would be painful to lose access to
- Be wary of social engineering, exercise caution with requests for information and promptly reset email password if you think you’ve been hacked
- Back up valuable data, potentially locally and in the cloud
- Be on the lookout for spam and phishing attempts by verifying the sender’s email address, checking for grammatical accuracy, and copy sent in image form




Leave a Reply
Want to join the discussion?Feel free to contribute!